In the quest of becoming more open and collaborative, networks have made systems more vulnerable to attacks. Uncertainty in regulatory policies by the government along with inadequate expertise in industrial IT network remains a significant restraint. Against this backdrop, organisations need to partner with a solutions provider who understands the industrial environment and is committed to cybersecurity. Some top notch solution providers in the cybersecurity space include Raytheon Cyber, EY, IBM Security, Mimecast, Cisco, CyberArc, Lockheed Martin, Delloite, and PwC. According to Cybersecurity Ventures, it has been predicted that cybercrime damages will cost the world $6 trillion annually by 2021, up from $3 trillion in 2016.
Our main objective is to evaluate and assess the current state of cybersecurity preparedness for SCADA systems in the Power Industry. Current controls that are being used are legacy systems that use commercial off-the-shelf products with known vulnerabilities. Earlier the SCADA systems were isolated but nowadays they are available via public networks such as Internet at a much higher degree. Due to the emergence of smart grids the ecosystems are under greater threat. Various initiatives are being taken over the past 5 years to increase the awareness and the preparedness against such threats.
Internally in an organization it can be difficult to track how different components of SCADA are connected, as several internal components are equipped with functions or services through which suppliers or control engineers can access them. This enables the staff and the external suppliers to install, update, and configure software across the Internet. Such components having these kind of remote management features are called Intelligent Electronic Devices (IEDs).
In today’s world, as the control devices are networked due to a common IT platform, networking hardware is used for communication with substation IEDs. These IEDs are a group of computers performing several ancillary functions in addition to their basic purpose of system protection.
Power generation is considered to be the most controlled or the least vulnerable to cybersecurity attacks as it is a closed loop setup. Though in Nuclear power plants, comprehensive risk assessment and implementation plans are required to safeguard information. Transmission grid is at the greatest risk due to multiple remote locations are taken into consideration. There are multiple physical locations to breach the network.
Some of the key pain points in the cybersecurity space in the power industry include lack of resources and unclear ROI. Lack of trained cybersecurity professionals and proper corporate support add to the problem.
The main types of attacks in the power cybersecurity market include:
- Internal Attacks
- ICS Firmware attacks
- Watering Hole attacks
- Operational Technology attacks through compromised corporate networks
- Automated attacks, malwares and botnets
Some of the key megatrends which will impact the cyber security market in more than one ways include:
- Urbanization
- Cyber warfare
- Space jam
- ‘Smart’ gadgets
- Electric Mobility
- New Business Models like ‘Value for money’, ’make 1 sell many’
The power cybersecurity market can be divided into six factors by priority, namely:
- Confidentiality which includes Data security
- Regulations which include compliance with NERC-CIP regulations and forthcoming rules
- Availability which signifies the system uptime
- Operational Safety which constitutes of safety of people, processes and environment
- Legacy Assets which constitute of the technology refresh for existing bulk electric systems (BES)
- Integrity which signifies system reliability, in the events of any cyberattacks.
Three types of solutions in the Power cybersecurity market are:
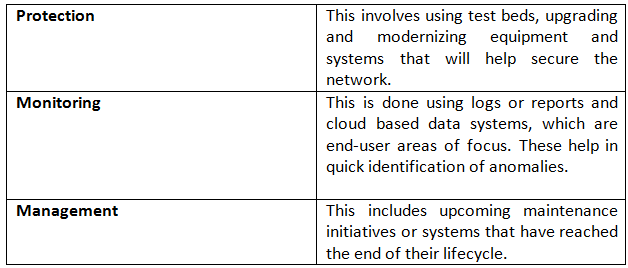
Flowchart depicting the concept of Security Intelligence
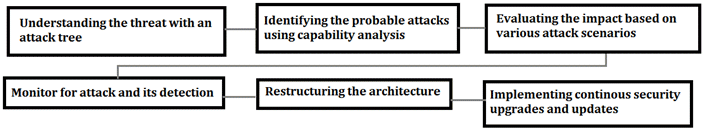
Some of the key strategies undertaken to reduce vulnerabilities include providing limited security clearances and remote access to a small number of highly trained employees. For smart grid security an algorithm is used to generate response based on previous experiences. This term is popularly coined as computational intelligence.
Some of the important Cybersecurity regulations that have been imposed on the Power Industry include FISMA (2002), FIPS 199 (2004), EPACT(2005),FIPS 200(2006),NERC CIP,IEC 62351,NIST SP 800-53 A,ISA 99 (2007),IEEE PSRC H13(2008),NIST SP 800-30,NIST SP 800-53A(2010),ISA/IEC62443,NIST SP 800-30(2012),NIST SP 800-53A(2013),NERC CIP v5(2014).
The best practice is to connect the control network to other network through the firewall, further connecting all other devices to only one network.
The security functionalities are slowly being integrated into a single platform, thus any vulnerability could expose the entire system to a cyber-attack. Due to this customers still prefer a layered defense that uses best of the solutions from various vendors.
Abbreviations Used
- SCADA: Supervisory Control and Data Acquisition
- ROI: Return on Investment
- IEDs: Intelligent Electronic Devices
- FISMA: Federal Information Security Management Act
- FIPS 199: Federal Information Processing Standard Publication
- EPACT: Energy Policy Act
- NIST: National Institute of Standards and Technology
- ISA: The International Society of Automation
- IEEE: Institute of Electrical and Electronics Engineers
Citations
- http://patriot-tech.com/blog/2015/10/27/common-scada-system-threats-and-vulnerabilities/
- https://www.nationalcybersecurityinstitute.org/energy-utilities/cybersecurity-challenge-protecting-electric-power-and-utilities/
- https://www-935.ibm.com/services/multimedia/WR928534SF-Best_practices_for_cyber_security_in_the_electric_power_sector.pdf